When a new vulnerability is made public, a Common Vulnerabilities and Exposures (CVE) number is assigned to it. A CVE will contain a brief description of a security vulnerability and is a way to uniquely ID each security vulnerability that may be found. These CVE numbers allow security professionals to track vulnerabilities, patches to fix the vulnerability and any malicious activity that may be tied to the CVE in a threat management, threat intelligence or risk management system.
When vulnerabilities are typically discovered, a non-malicious proof of concept is usually shared with the security community to demonstrate the severity of a vulnerability or how trivially easy it could be exploited. Security professionals and researchers will often seek out such proof of concepts to develop counter or detection mechanisms to stay head of adversaries.
Recently Microsoft disclosed 2 vulnerabilities which affect Microsoft Exchange Servers and can allow for remote code execution. From Microsoft’s Blog:
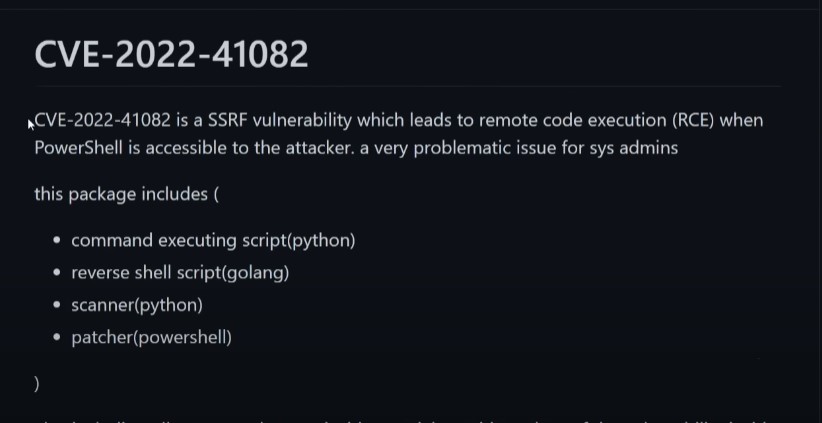
Microsoft is investigating two reported zero-day vulnerabilities affecting Microsoft Exchange Server 2013, Exchange Server 2016, and Exchange Server 2019. The first one, identified as CVE-2022-41040, is a Server-Side Request Forgery (SSRF) vulnerability, and the second one, identified as CVE-2022-41082, allows Remote Code Execution (RCE) when PowerShell is accessible to the attacker.
Currently, Microsoft is aware of limited targeted attacks using these two vulnerabilities. In these attacks, CVE-2022-41040 can enable an authenticated attacker to remotely trigger CVE-2022-41082. It should be noted that authenticated access to the vulnerable Exchange Server is necessary to successfully exploit either vulnerability.
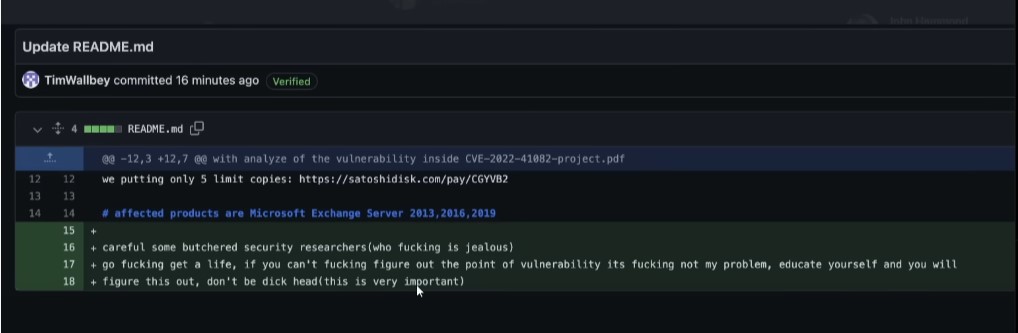
To take advantage of the high interest in these vulnerabilities which at time of writing have not been patched yet, scammers have been creating false proof of concept repositories on code hosting sites like GitHub. This practice of creating repositories to take advantage of the interest in a vulnerability is not new, however there has been a significant increase in this activity with the Microsoft Exchange vulnerabilities.
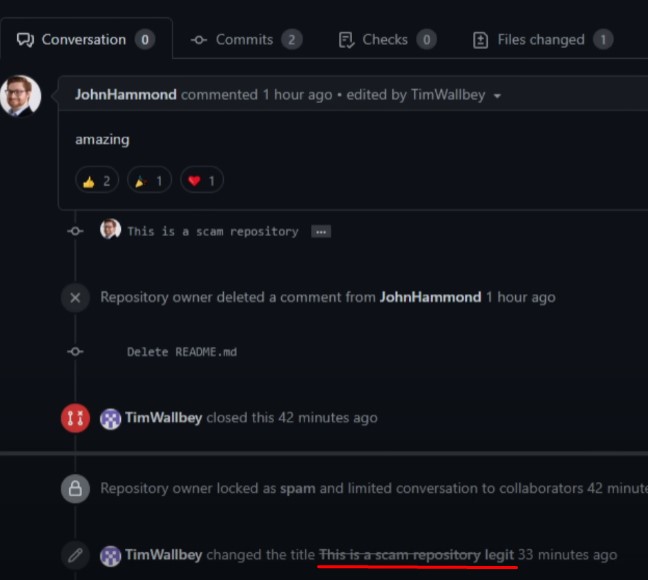
This was first noticed by security researcher John Hammond who found dozens of GitHub repositories with names containing the CVE numbers of the Exchange vulnerabilities along with text like POC or exploit. In each of these repositories, users are directed to Satoshi’s Disk, a site which bitcoin can be exchanged for access to files, where payment of around $100 is requested for access to the proof of concept for these vulnerabilities. However, the POC or exploit does not exist once payment is made as this is a scam.
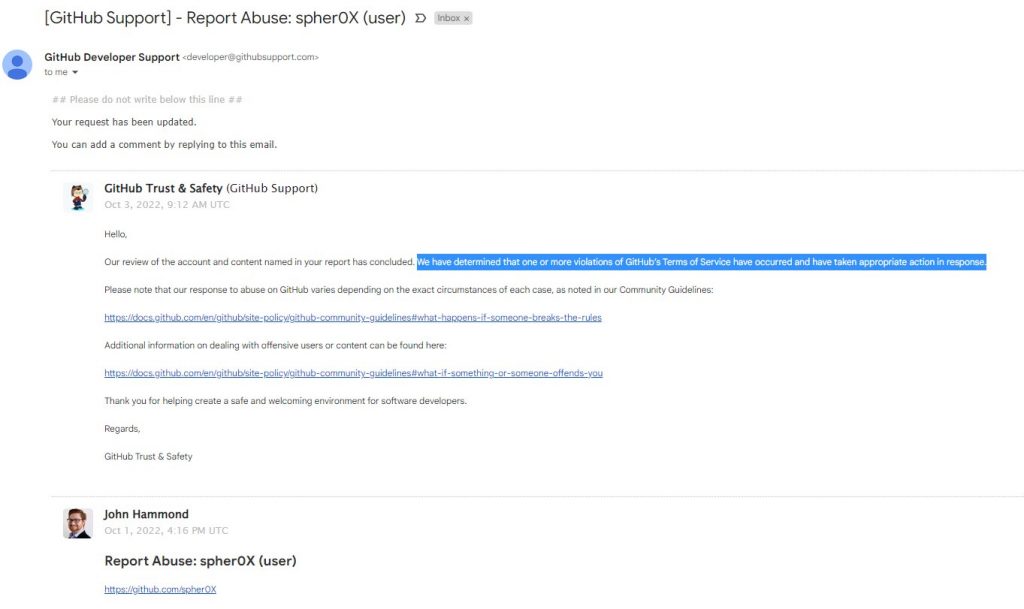
John has been reporting these repositories to Github and they have been quick to take down these repositories. What John also found is that if he created an issue or pull request to warn others that this is a scam, the scammer would disable issues and would change the title, text of the pull request.