MGM Resorts and Caesars have been hit by a cyberattack in which ransomware was deployed and has taken multiple of their systems offline across several hotels and casinos that they operate. The initial access tactic was social engineering which has prompted inquiries regarding past actions associated with malicious actors and the weak points they exploit. Security experts increasingly believe that the AlphV group, also referred to as BlackCat, which claimed responsibility for the MGM assault, has collaborated with Muddled Libra. The attackers demanded a $15 Million ransom from both MGM and Caesars, Caesars paid the ransom while MGM did not.
Jason Koebler visited the affected casino and published a good writeup on 404 Media (excerpt):
Las Vegas’s hottest new attraction is an interactive ransomware exhibit, currently playing out across every MGM property in the city. To experience what it’s like to gamble in a series of hacked casinos, I got on one of the first flights out of Los Angeles Saturday morning with the goal of figuring out not just how screwed up the casinos were, but also to witness the marvelous ability of the human species to adapt and cope with bizarre circumstances.
Last week, the ransomware gang ALPHV hacked Caesars and MGM, taking down multiple systems across the casino giants’ networks. Caesars folded quickly, and paid a $15 million ransom, helping return everything to normal for their customers. MGM, meanwhile, is refusing to pay, meaning that all sorts of things are broken at its 14 hotels and casinos in Vegas, including the Bellagio, Aria, MGM Grand, NoMad, and Mandalay Bay.
The attack has affected 14 hotels and has a major impact on revenue generating operations and has lead to a very bad guest experience at these hotels. The attacks have been collectively attributed to AlphaV, Muddled Libra and Scattered Spider as evidence emerges that these groups collaborated with each other to pull of the attacks.
From Palo Alto’s blog:
Unit 42 researchers and responders have investigated more than half a dozen interrelated incidents from mid-2022 through early 2023, which we’ve attributed to the threat group Muddled Libra. This threat group favors targeting large outsourcing firms serving high-value cryptocurrency institutions and individuals. Thwarting Muddled Libra requires a combination of tight security controls, diligent security awareness training and vigilant monitoring.
Muddled Libra’s tactics can be fluid, adapting quickly to a target environment. They continue to use social engineering as their primary modus operandi, targeting a company’s IT help support desk. For example, in under a few minutes, these threat actors successfully changed an account password and later reset the victim’s MFA to gain access to their networks.
One noticeable change of TTP is the heavy use of anonymizing proxy services. Attackers are using these proxy services to obscure their IP addresses and appear to be in a local geographic area. In the cases we’ve recently been involved with, we observed Muddled Libra performing the following activities:
Using NSOCKS and TrueSocks proxy services
- Creating email rules to forward emails from specific security vendors to the actors to monitor communications and those helping in the investigation
- Deploying a custom virtual machine into the environment
- Using an open-source rootkit, bedevil (bdvl) to target VMware vCenter servers
- Gaining administrative permissions
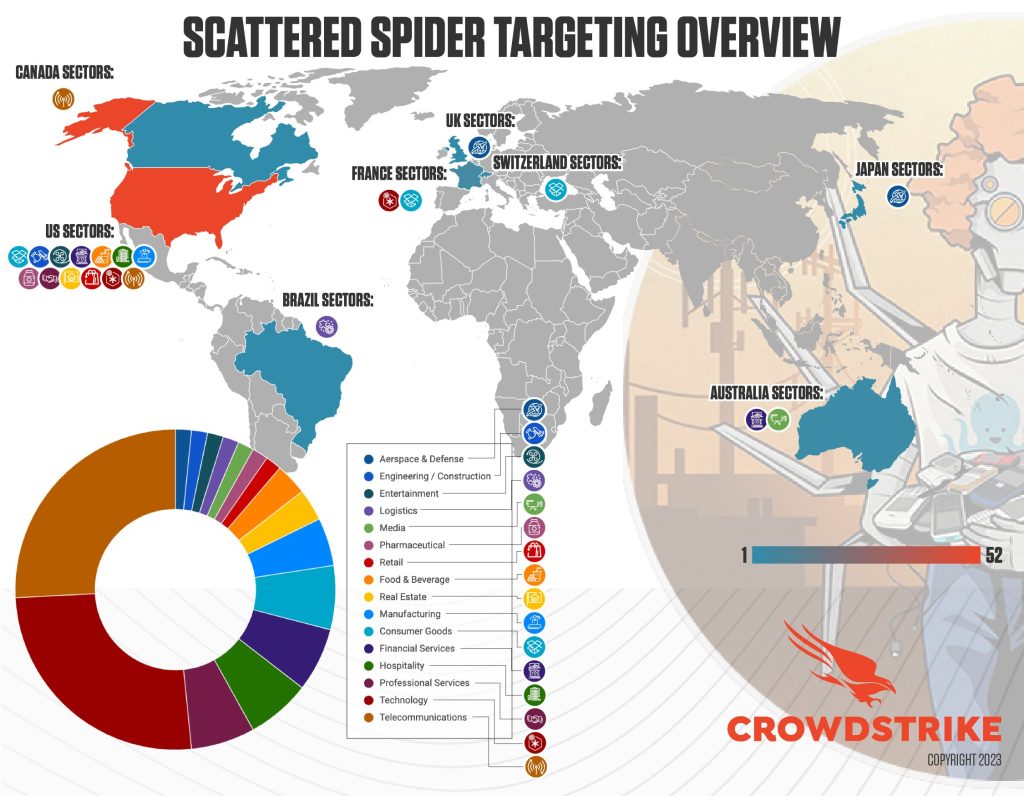
Sector targeting published by CrowdStrike: