In a report published by Citizen Lab, details have emerged how the presential candidate Ahmed Eltantawy has been targeted with predatory spyware made by Cytrox. The spyware was sent to Ahmed via SMS and WhatsApp after he announced his intention to run for president of Egypt. The report sheds light on how the candidate’s phone was selected for targeting via network injection and redirected his browsing to a malicious website that would infect his phone with Cytrox’s Predator Spyware.
Citizen Lab worked with Google’s Threat Advisory Group (TAG) to obtain the iPhone zero-day exploit chain which consisted of three vulnerabilities (CVE-2023-41991, CVE-2023-41992, CVE-2023-41993) and can say with high confidence that the Egyptian government was behind the attack.
The three vulnerabilities that were uncovered are as follows:
- CVE-2023-41991 (Security): A malicious app may be able to bypass signature validation.
- CVE-2023-41992 (Kernel): A local attacker may be able to elevate their privileges.
- CVE-2023-41993 (WebKit): Processing web content may lead to arbitrary code execution.
From Citizen Lab’s Blog:
The zero-day chain was hosted on sec-flare[.]com, and also contacted verifyurl[.]me. We fingerprinted these two websites (fingerprint F1 for sec-flare[.]com and F2 for verifyurl[.]me). We have identified a large number of IPs that matched our fingerprints, using Internet scanning. We consider all of these IPs (and the domain names returned in TLS certificates when they matched our fingerprints) to be linked to Cytrox’s Predator spyware. While we investigate further, we are not releasing the domain names or IP addresses at this time.
Some of the domains we identified had names suggestive of tailoring towards specific countries or regions of focus include the Arabian Gulf, Southeast Asia, Angola, the Democratic Republic of the Congo, Egypt, Greece, Indonesia, Kazakhstan, Madagascar, Mongolia, the United Arab Emirates, and Sudan, which is a reported Cytrox customer. Of course, we cannot necessarily conclude that all of these governments are customers.
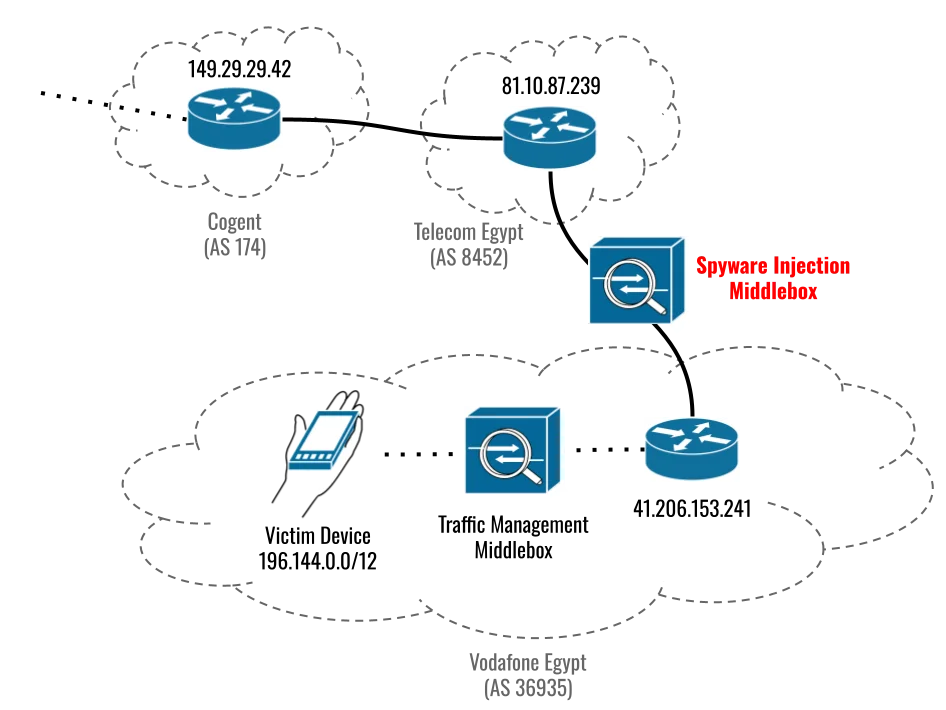
We conducted a test to understand where in the network the injection happened. Ultimately, we were able to localize the injection to a link between Telecom Egypt and Vodafone Egypt. We cannot conclude from technical data alone whether the middlebox sits on the Telecom Egypt side or the Vodafone Egypt side of the link. However, we suspect that it is within Vodafone Egypt’s network, because precisely targeting injection at an individual Vodafone subscriber would require integration with Vodafone’s subscriber database.
Also, given that the injection is operating inside Egypt, the spyware is sold to government agencies, and Egypt is a known Predator customer, it is highly unlikely that this targeting occurred and that this setup was established outside of the purview of Egyptian authorities.